OCF-over-Thread
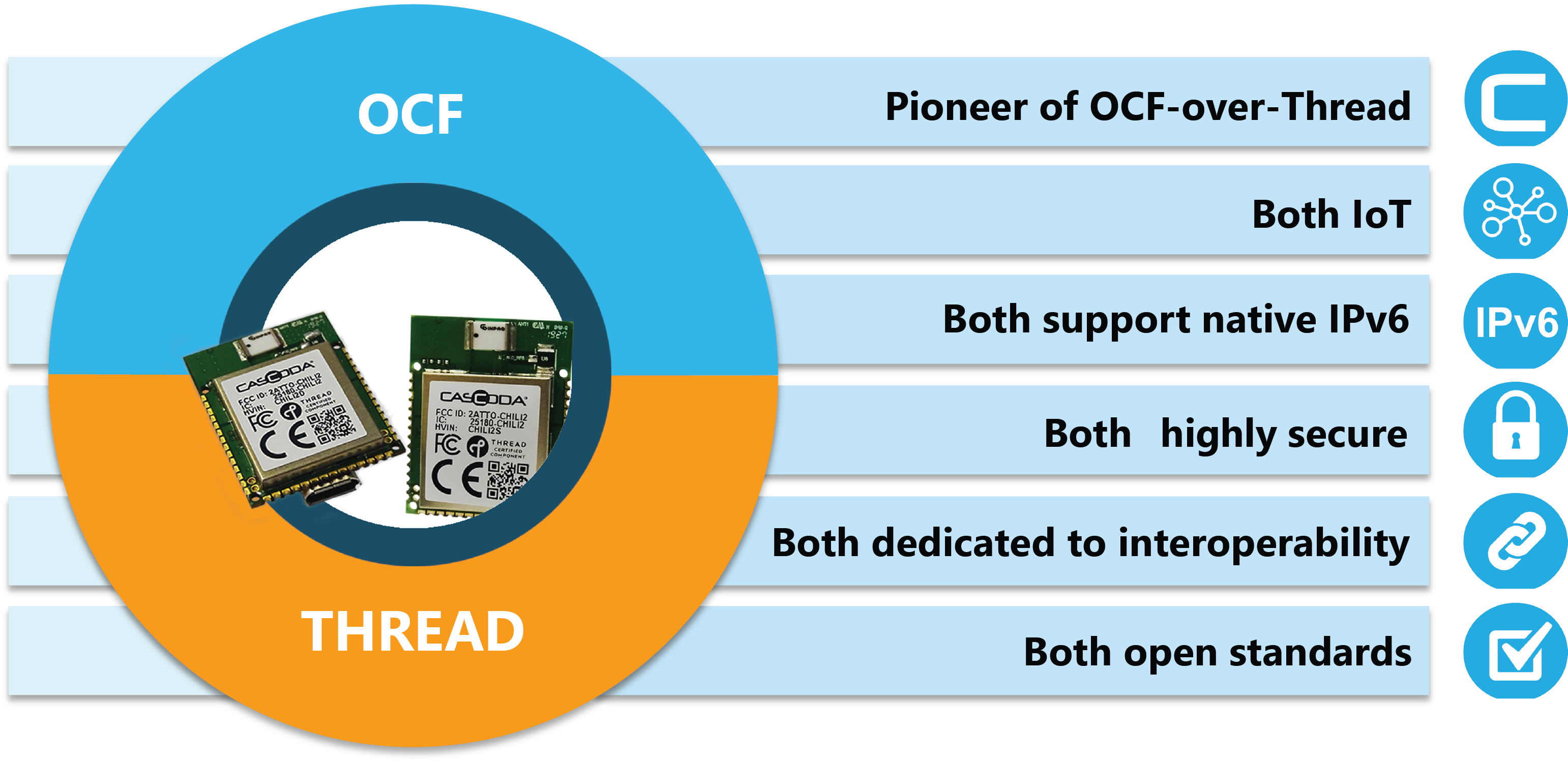
Cascoda pioneered the development of OCF-over-Thread. OCF and Thread are open standards based on the universally-supported Internet Protocol (IP). As such, both standards are dedicated to interoparability, both are built for IoT, both support native IPv6 communications and both use Datagram Transport Layer Security (DTLS) security features as standard.
Overview
The Open Connectivity Foundation (OCF) is a standards organization that develops application-layer IoT protocols, based on the Internet Protocol (IP), using strong open standards. IoTivity® is the open source reference implementation of the OCF specification. IoTivity® provides a framework for device discovery, on-boarding, end-to-end security (and optionally, data models), for device-to-device and device-to-cloud connectivity. OCF is published as a ISO/IEC specification, and there is a comprehensive certification program in place.
-
Cascoda® & OCF®
Pioneer of OCF-over-Thread & Chair of Technology Steering Committee & the MARCOM Work Group -
Device-Device Connectivity
Device-device connectivity,
across any IP Network -
Device-Cloud Connectivity
Device-Cloud connectivity
for any OCF device -
Highly Secure
Supports Public Key Infrastructure (PKI) security -
Dedicated to Interoperability
Device-to-device & device-to-cloud -
Open Standards
Platform agnostic (iOS, Android, Linux, Windows, Embedded etc.)
OCF Security
OCF, as an IP-based application layer, ensures that the data sent over the internet, whether device to device, or device to cloud, cannot be read or modified by anyone except the desired recipient. This security system is called end-to-end encryption. End-to-end encryption is important, because information exchange over the internet may pass through the networks of intermediary organisations such as telecom and internet providers in multiple jurisdictions worldwide.
OCF achieves end-to-end encryption using a set of policies and procedures known as Public Key Infrastructure (PKI). PKI defines how to employ public and private digital certificates to perform end-to-end encryption. OCF employs a communications protocol known as Datagram Transport Layer Security (DTLS) to exchange PKI public key certificates between the OCF client and OCF server. Both the OCF client and server then use the public key certificates of the respective recipient to securely encrypt the data to be sent, such that the recipient is the only one that can read it.
The OCF specification maps to the IoT baseline security capabilities consensus outlined by the US, UK and EU authorities:
National Institute for Standards and Technology (NIST) NISTIR 8259 draft of recommendations IoT device manufacturers
The Consumer Technology Association (CTA) C2 Consensus on IoT Device Security Baseline Capabilities
UK's Code of Practice for Consumer IoT Security
European Union Agency for CyberSecurity (ENISA) Baseline Security Recommendations for IoT
European Telecommunications Standards Institute (ETSI) Baseline Security Requirements for IoT
as described here.
In addition, Cascoda's OCF-over-Thread solution has achieved the highest (Gold) standard of IoT security according to the IASME 'IoT Security Assured scheme'. This scheme is aligned with the ETSI technical standard for IoT security, EN 303 645, and with the proposed UK IoT security legislation and guidance. It is also mapped to the IoTSF Security Compliance Framework. Click on the certificate below for further information:
OCF Clients & Servers
-
OCF Roles
The OCF Architecture defines two logical roles that a device can take:
OCF Server: Devices that expose hosted resources, is discoverable and responds to client transactions
OCF Client: Devices that interacts with resources on an OCF Server using Create, Retrieve, Update, Delete and Notify (CRUDN) commands
An OCF Device may implement one or both logical roles -
Optimized for IoT
RESTful interaction model using CoAP
CoAP used to push events from server to client, to avoid polling
Built-in discovery and subscription mechanisms -
Encoding Scheme
Concise Binary Object Representation (CBOR) based on a JSON data model
The simplicity of JSON with the advantage of binary payloads